Custom Monitoring with Microsoft Sentinel Watchlists

Import Custom Data from Functionally Anywhere.
Microsoft Sentinel users were recently given the option to insert their own data into Sentinel using Watchlists. This has opened a world of possibilities for security analysts and admins alike because they can include data that they have gathered from functionally any area they can think of to improve the quality of their detections and investigations.
In this blog, we show how you can use watchlists to add useful data to your Microsoft Sentinel environment. We will also discuss how cybersecurity analysts can use that data to help with their investigations once the watchlists are made. There will also be a brief section at the end that discusses how to translate data in unconventional file formats into watchlists.
Custom IOCs
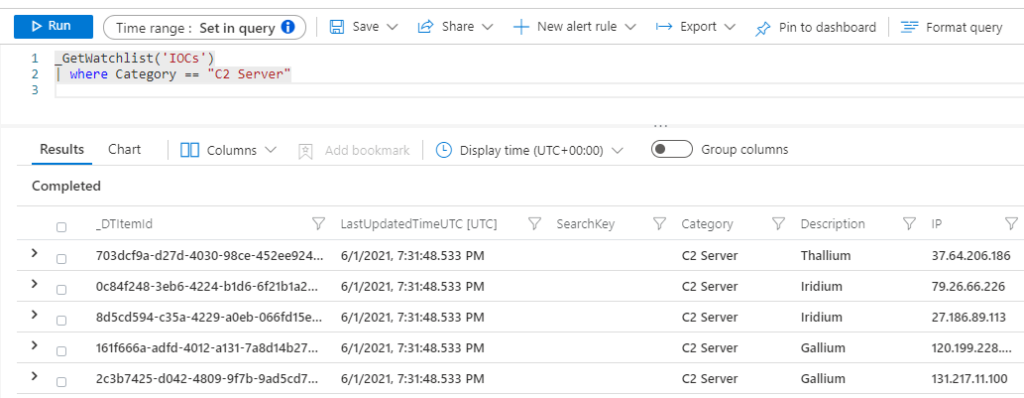
The original intention of watchlists was to give security admins and analysts a way to import their own IOCs (Indicators of Compromise) into Sentinel. Cybersecurity analysts can cross-reference the IOC lists when looking for signs of malicious activity. The IOC lists can also be used in analytic rules to generate incidents based on the type of IOC found.
User Attribute Lists
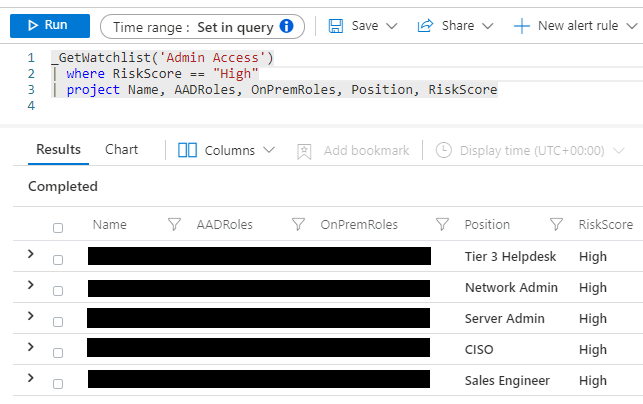
There is only a limited amount of user information available in Microsoft Sentinel, and it may not be enough for analysts to conduct their investigations. For instance, it is important for analysts to know what kind of access the user has in potential account compromise incidents,.
Creating a user attribute watchlist will allow analysts to query about any information that is available in the user attribute table. In the example image, the analyst can quickly see the position, AAD roles, and on-premises roles of important admins in their organization.
Exception Lists
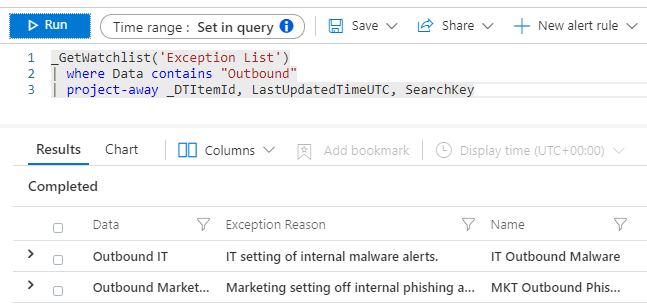
A SOC typically manages millions of alerts, and there is not a readily available solution in the Microsoft products that they can use to suppress the alerts without risking unintended consequences. Creating an exception watchlist allows analysts to create their own custom indicators that they can use to customize what kind of alerts will get suppressed.
Fill in Holes Where Data is Missing
Some of the data sources connected to Microsoft Sentinel do not provide all the information needed to finish an investigation. An example of this is Microsoft Defender for Cloud because it has limitations in identifying who was involved with an incident. By creating a watchlist used to fill in missing data, analysts can finish more of their investigations without having to go perform advanced threat hunting.
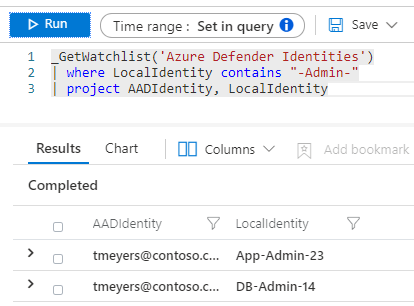
Supplement Data from 3rd Party Products
Some analysts may not be able to understand what information coming from 3rd party products means. These analysts can get help understanding these terms by having a custom watchlist available that is able to quickly explain what the messages from these products mean without having to spend 15+ minutes googling it.
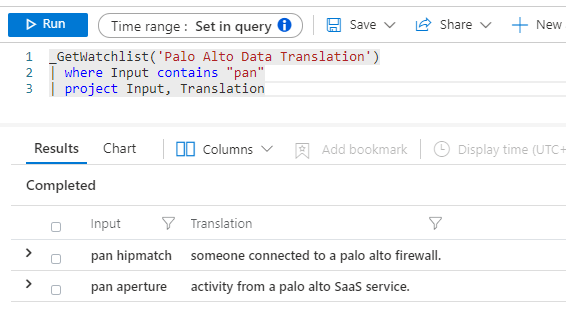
Import Data in Obscure File Formats
Most of the data that security analysts and admins have available will not be in the form of a CSV file that can be easily imported as a watchlist. Luckily, there are several creative methods that you can use to transform files from any file with text into CSV.
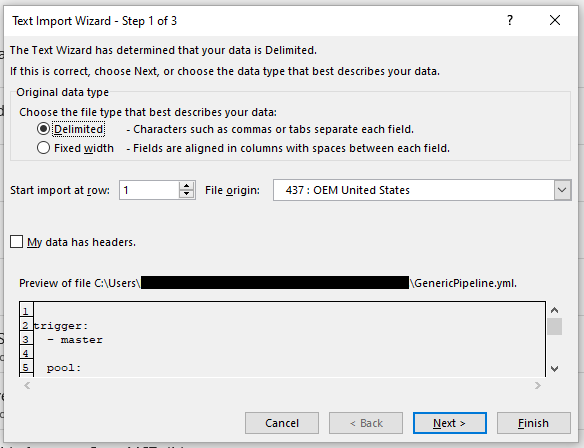
There are CSV file converters that can be found online, and Office apps have compatibility options like the Text Import Wizard that can be used to get files that Office apps do not normally recognize into an Excel spreadsheet so it can be saved in a CSV format.
We will continue to share best practices and lessons learned in future posts on importing data into Microsoft Sentinel. Watchlists are just one of the many features that the Microsoft Sentinel developers are releasing to make security data monitoring easier and more effective.
In closing, consider these three questions when using Watchlists in your organization:
- Do we have any useful security data lying around that we could convert into a watchlist?
- Can we create new analytic rules now that the option to import new custom data is available?
- Will we be able to train analysts to use the custom data while doing advanced hunting?
