Use JSON to Improve Microsoft Sentinel Operations

Be more efficient and unlock new tools with JSON.
When working on security in Microsoft Sentinel it is important to understand how the components of the platform work. JSON is one of the major components of Microsoft Sentinel because it uses value pairs to communicate how some of the most important features are supposed to behave.
In this blog, we show how a Microsoft Sentinel user can use JSON files to improve their effectiveness when working with features in Microsoft Sentinel. We will also go over some of the configurations in Microsoft Sentinel that are only possible if the user understands how to use JSON.
JSON for Microsoft Sentinel Playbooks
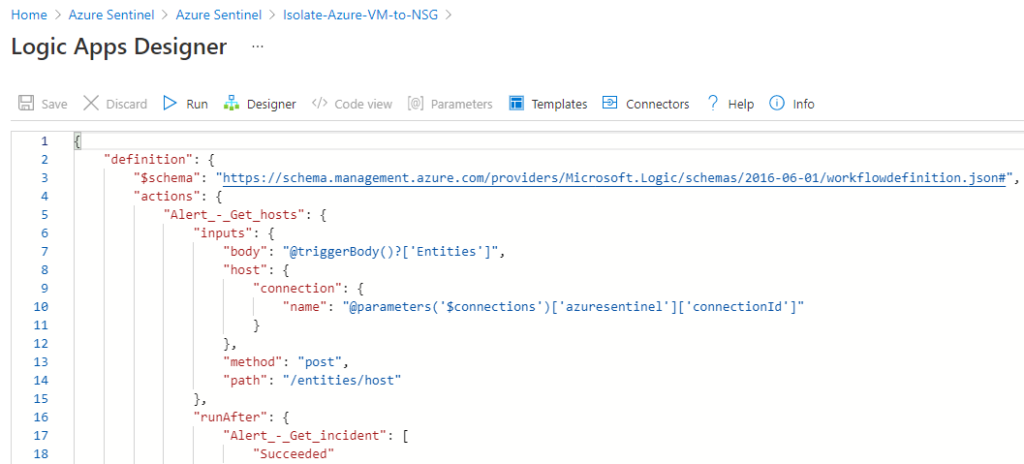
JSON is used to write ARM templates for playbooks in Microsoft Sentinel. Understanding how to use JSON enables copying, editing, and sharing Microsoft Sentinel Playbook ARM templates to public GitHub repositories.
You can also edit more complex playbooks because you will have an understanding of the configurations that make the playbook operate. The JSON for playbooks can be edited in the “code view” menu when editing a playbook.
JSON for Microsoft Sentinel Workbooks
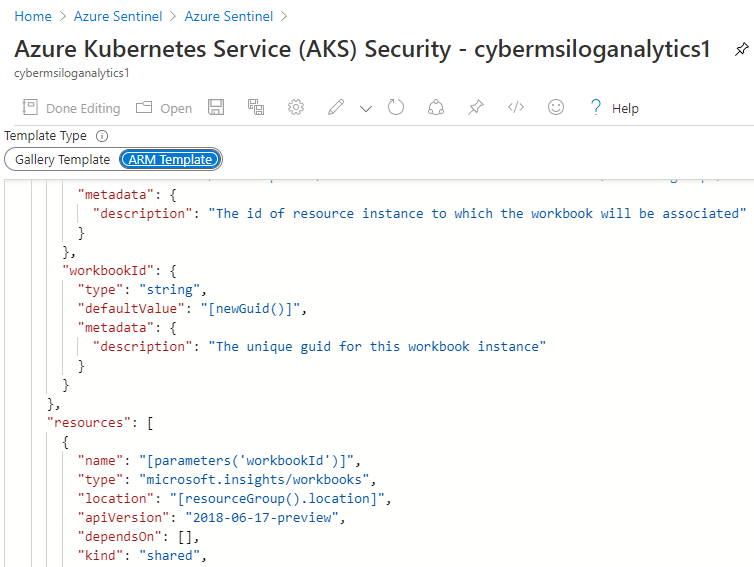
JSON is also used to write ARM templates for workbooks in Microsoft Sentinel. When you know how to use JSON, you can use as well as share workbooks available in public GitHub repositories.
You can also develop or modify more complex analytics because you understand the structure of workbooks. The JSON for workbooks can be edited in the “advanced view” menu while editing a workbook. Switch the slider to the “ARM Template” to get the ARM version.
JSON for Microsoft Resource Deployment
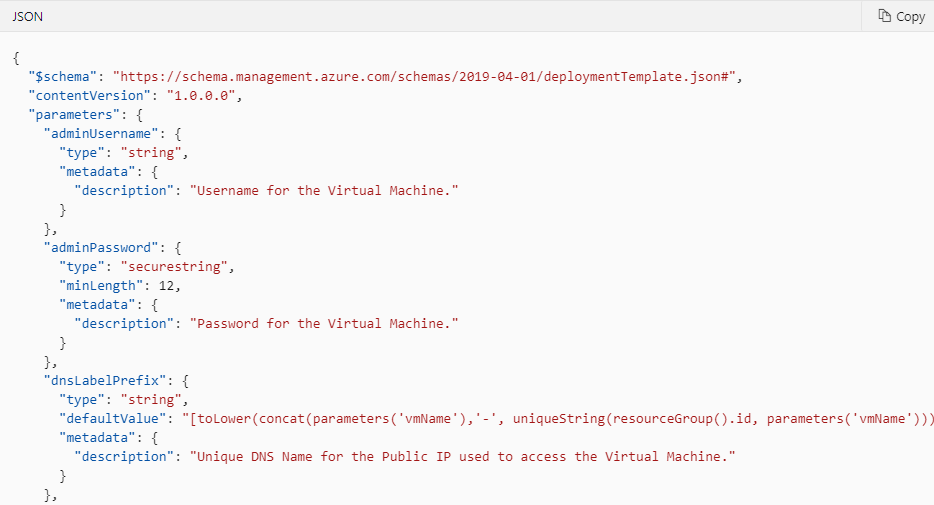
As a cybersecurity analyst, you use Microsoft Sentinel to monitor various resources that are deployed to the cloud. You are able to help IT admins in their environment with creating ARM templates for resources that are more secure.
ARM templates can deploy resources from other areas of Microsoft with extensions so that they can be monitored right away. Some of the most useful security extensions include Microsoft Defender for Cloud extensions that can send data to Microsoft Sentinel for analysis and Microsoft monitor extensions that gather data that is useful for advanced threat hunting.
JSON to Get More Data from Tables
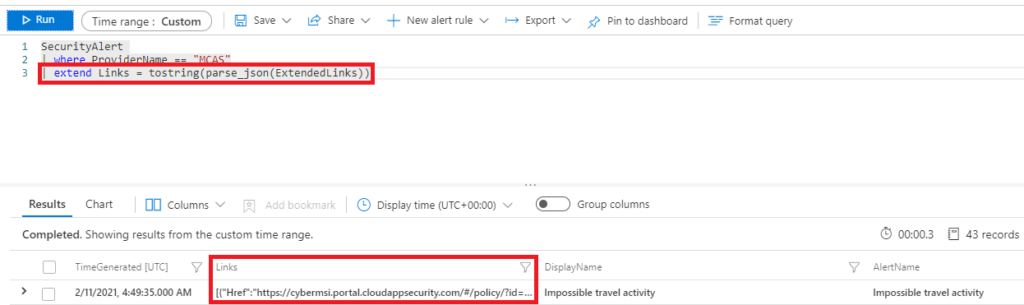
Some tables in Microsoft Sentinel contain truncated data that can be viewed by selecting one of the results of a query. This extra data hidden inside the table can be viewed and used as if it were any other data in the table by using the “parse_json()” function. This unlocks data like additional event details, information about associated entities, and links to other Microsoft security UIs that are all useful for investigations.
JSON for Custom Data Connectors
Multiple custom data connector options require the use of JSON so that the data being collected can be used with Microsoft Sentinel. By knowing how to use JSON with data sources that do not have a data connector yet, security analysts can connect many more types of data sources to Microsoft Sentinel for monitoring.
We will continue to share best practices and lessons learned in future posts on customizing Microsoft Sentinel in customer environments. Microsoft Sentinel will continue to release new features and knowing JSON will help us use and expand upon those features.
In closing, consider these three questions when using JSON for Microsoft Sentinel in your organization:
- Can we use JSON tools like ARM templates to make the resource deployment process more effective?
- Is there a way to improve our existing Microsoft Sentinel tools using the JSON resources that are currently available online?
- Should we assign someone on our team to learn more about using JSON in Microsoft Sentinel to improve our efficiency and security?
