Advanced Threat Hunting in Microsoft Sentinel.

When Existing Data isn’t Enough, Look for Metadata.
Microsoft Sentinel has a constantly expanding list of advanced hunting queries that Microsoft has gathered from around the community to help with finding useful information when investigating cybersecurity incidents. As of the last count, there are 200+ queries available out-of-the-box in Microsoft Sentinel. It is worthwhile to quickly find queries that can help with investigations, which may not be completed timely otherwise.
Cybersecurity analysts at CyberMSI have run into a sizable percentage of incidents that were not solvable with the given information that was provided in the default investigation views. To get around this issue, our analysts had to sometimes create queries on their own to find the remaining information they needed. Analyst productivity could have gone up considerably if some of these advanced hunting queries were available for them.
In this blog, we highlight the most useful queries that we use in our SOC. All these queries come with Microsoft Sentinel by default, so there is no need to do additional query writing unless someone is interested in customizing the query for a specific purpose.
Login Attempts Using Legacy Authentication
A common way to gain access to an endpoint or service is using a “downgrade attack”, where a malicious actor uses an authentication method that uses an older standard to circumvent security controls. This query looks for patterns in the sign-in logs table that would be considered signs of legacy authentication being used. This is useful for determining how a malicious actor might have gained access to something without being stopped by existing security controls.
Encoded PowerShell Commands
By encoding a PowerShell command, malicious actors can evade less advanced security controls. MDE and Microsoft Defender for Cloud detect activity in encoded PowerShell, but all other Microsoft devices that do not have these enabled may not be able to detect what happens in encoded PowerShell commands. This query looks for encoded PowerShell activity in the Security Events table. This is useful for helping security analysts look for obfuscated PowerShell activity happening around the time of their incidents.
Double File Extensions
By adding a second file extension to the end of a file, a malicious actor can both evade some security controls and trick users into opening a file thinking that it only had the extension at the end. This query only looks in the Office Activity table for EXE files in SharePoint. What is nice about this query is that it can be used as a template to look for all kinds of double extension files in Office apps. An analyst that understands queries can play “Mad Libs” with the query. Functionally “Look for <file extension> in <Office app>”.
NSG Admin Activity
If a malicious actor gains access to a cloud environment, one of the easiest ways that they could get persistence or move laterally is by changing network rules. Internal users can also unintentionally create vulnerabilities by changing network rules for their resources. This query looks for network security group administrative activity in the Microsoft Activity table. By going over recent NSG activity, analysts can discover important details about what happened on the virtual networks associated with their incidents.
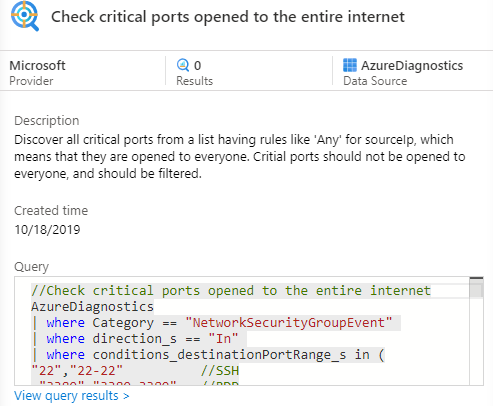
Critical Ports Open to the Internet
Open ports are a common angle of attack because they are easy to find when doing reconnaissance. If a malicious actor finds a critical port that is open to the internet, they are going to at least attempt to exploit it. This query looks through the Microsoft Diagnostics table to find ports open to the internet that Microsoft considers critical. An analyst can use this query to help determine the attack vector for the incident, and they can use it to help with security recommendations in post-incident discussions.
We will continue to share the latest and greatest Microsoft Sentinel features used in our customers’ environments. The cloud security environment will continue to get more complex as time goes on and features like shared hunting queries help cybersecurity professionals keep up with the latest cyberattacks.
In closing, consider these three questions when using the Microsoft Sentinel advanced threat hunting queries in your organization:
- Has anyone in the organization gone over the available advanced threat hunting queries?
- How do we react to incidents that do not have enough information, and can we use advanced queries to improve our incident resolution rate?
- Is there anyone on our SecOps team who can create advanced hunting queries using Kusto Query Language (KQL) to help with investigations?
