More Essential Microsoft Sentinel Automations

Enhance incident response with new automated tools.
In the previous Essential Microsoft Sentinel Automations blog we discussed the most important automations a SOC should have. Many automations have been created since then, and now we are going to share the newest automations that your Microsoft Sentinel SIEM instance should have.
In this blog we will discuss new automations that have been developed for Microsoft Sentinel over the last 6 months. We will also discuss how these automations can be implemented and utilized by analysts in your Microsoft Sentinel SIEM.
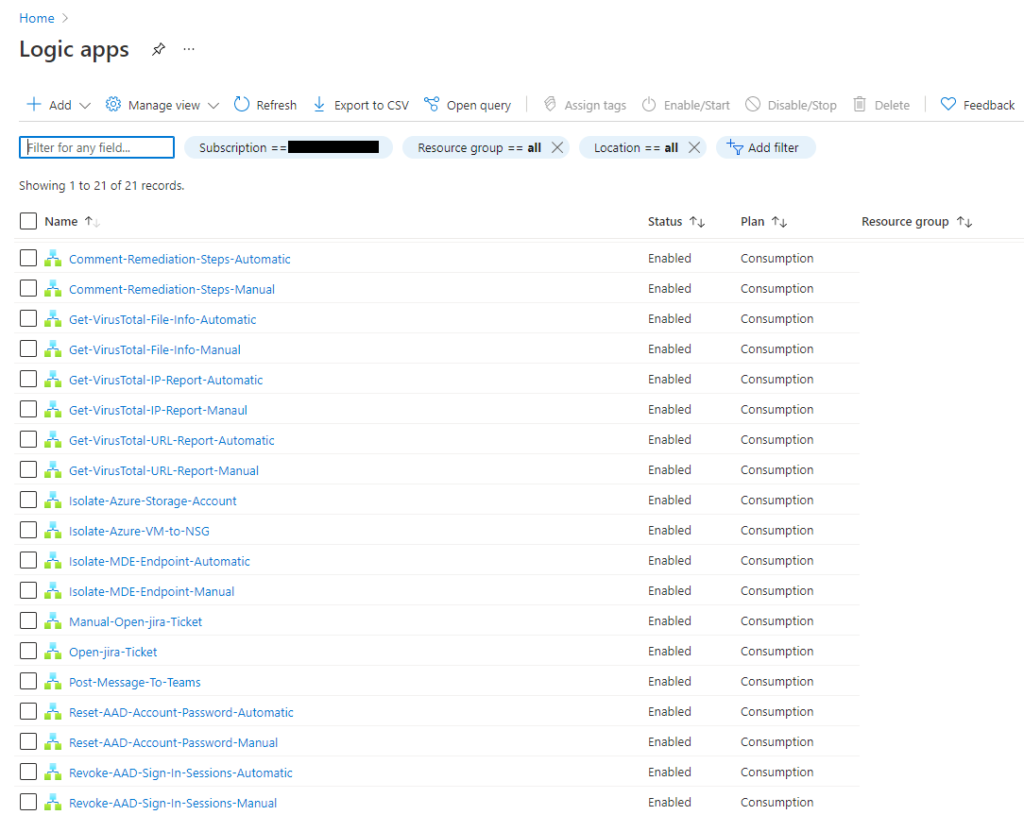
Manual and Automatic Triggers
When Microsoft Sentinel playbooks were still in preview, there was a significant amount of confusion about which automations triggered automatically after an incident and which ones were triggered manually. Now that most Microsoft Sentinel users understand the difference, they are writing their playbooks to include an automatic and manual trigger options.
When implementing the new automatic and manual trigger automations in your instance of Sentinel, the security engineers responsible for the SIEM should consider looking through new and existing versions for the automatic and manual versions of the automation.
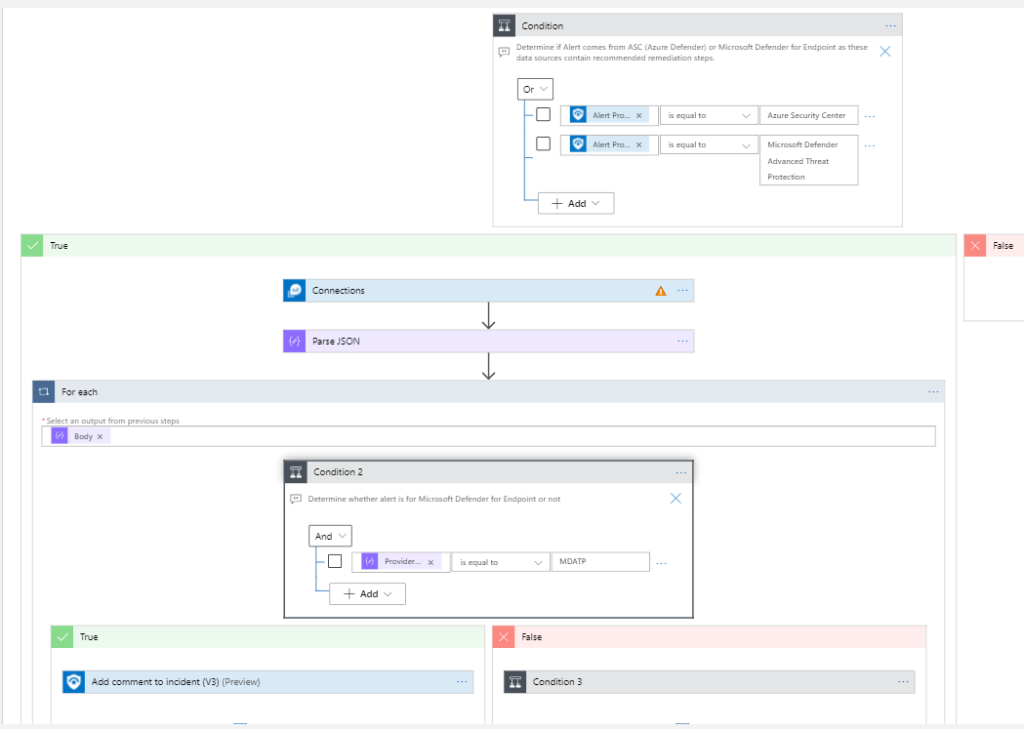
Comment Remediation Steps
Instead of having analysts always go to the other Microsoft XDR UIs (User Interfaces) to find recommended remediation actions, they can instead use an automation to create a comment in Microsoft Sentinel. This automation only works for Defender for Endpoint and Microsoft Defender for Cloud because those are the only UIs that have recommended actions in their tables.
Check for IOCs in Virus Total
Virus Total is a prominent source of free threat intelligence that many analysts use to compare IOCs that they have found during an investigation. This automation takes an entity recognized by Microsoft Sentinel and checks to see if it is a known IOC in Virus Total.
This automation requires an API key from Virus Total to work, if a security engineer in your organization has worked with Microsoft Sentinel notebooks before, they should already have a Virus Total API key available to use.
Isolate Other Azure Resources
The Isolate VM automation is an important automation for incident containment in Microsoft, and because of how useful it is the idea was expended upon to include new Microsoft resources. The new Isolate Storage Space automation allows analysts to isolate storage spaces to help with incident containment in Microsoft.
Both the VM and container isolating automations use HTTP action pieces to tell Microsoft to isolate the Azure resource. This same technique can likely be applied to all the other resources in Microsoft Sentinel, so if there is a creative security engineer in your organization, they can create new versions of this automation for each type of Azure resource.
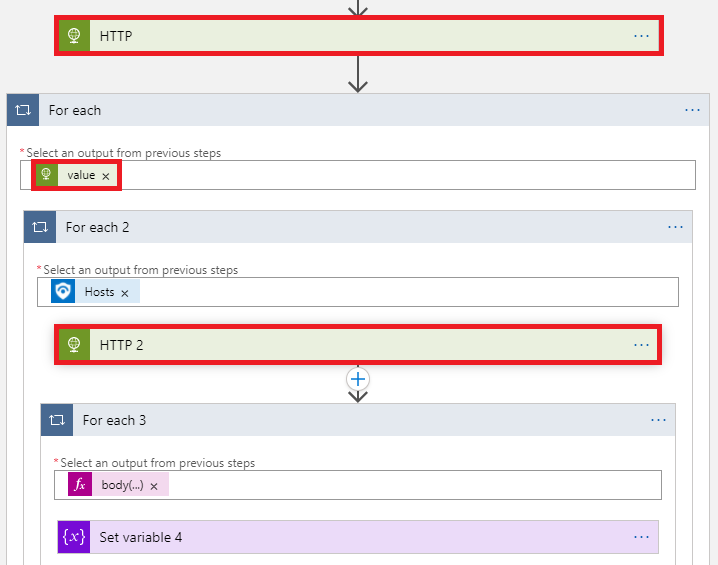
MDE Incident Response Actions
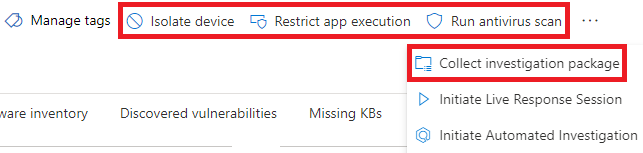
To save analysts the trouble of moving between UIs, 4 of the 6 incident response actions available in Defender for Endpoint now have automations that can run from Microsoft Sentinel playbooks. These automations can noticeably improve KPIs for containment and mitigation because the analyst no longer needs to leave the Microsoft Sentinel UI.
The automation applies the remediation action by using a for-each loop for each device entity recognized by the Microsoft Sentinel incident. If only some of the endpoints need remediation analysts will need to go to the 365 Security menu to take remediation actions on only some of the endpoints.
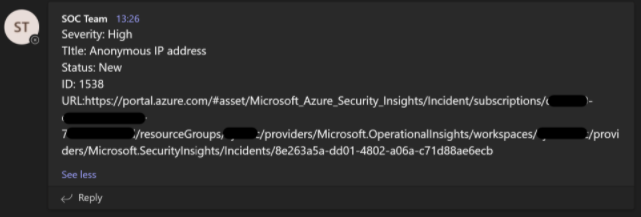
Post a Message to Microsoft Teams
The Microsoft Sentinel development team has been pushing to make investigation more collaborative using the Microsoft Teams app. They have added an option to create a Teams group message using the UI and a playbook that creates a Teams group message.
We will continue to share best practices and lessons learned in future posts on using Microsoft Sentinel automations in customer environments. CyberMSI and the Microsoft Sentinel community are constantly developing automations to help make incident management more efficient.
In closing, consider these three questions when adding new Microsoft Sentinel automations in your organization:
- Has anyone in our organization looked through the official Microsoft Sentinel GitHub recently for automations we can use?
- Are there any creative ways that we can edit the existing automations we have so that they can do other useful tasks for us?
- Can we use automations to reduce the need to move between the 6 Microsoft UIs needed to investigate different XDR incidents?
