Threat Vector: Network Scanning

Poor configuration could lead to malicious actors knowing your network better than your admins.
Network scanning is an essential active reconnaissance tool used when looking for avenues to breach an organization. If network and security admins do not have a solid understanding of network scanning and how to reduce the impact of the scans, malicious actors could learn everything they need to know about your network in a matter of hours.

In this blog we will discuss why network scanning is an important threat vector that network and security admins should be aware of. We will also discuss potential mitigations that you could implement to reduce the impact of network scanning in your environment.
Insufficient Perimeter Controls
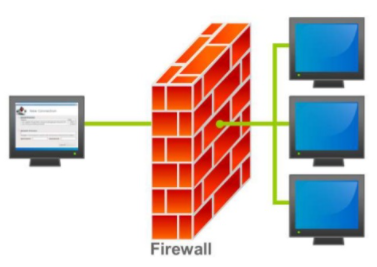
There are a surprising number of small and mid-sized organizations that haven’t correctly designed and configured perimeter firewalls, and this is an opportunity for malicious actors that want to peek inside. With nothing at the boundary there is nothing stopping them from scanning as much as the devices inside the network will allow.
The mitigation for this threat vector is to have someone with network security experience appropriately design, deploy and update the firewall rules at the boundary so that your network cannot be scanned as easily. This does not necessarily have to be a dedicated boundary firewall; modern network devices have built-in firewalls that can act as a boundary firewall.
Unexpected Network Access Points
Over the internet is not the only way someone can scan your network. There is a possibility that someone could come by one of your corporate buildings to see if they can access a network there. A wireless connection that reaches outside the building, or an open ethernet jack near an entrance can both be used as entry points to start a scan.
The mitigation for this threat vector is to have someone with red team experience evaluate the potential for someone that visits your building(s) to gain access to the network in unintended ways. Reducing the potential ways someone can gain access to the network physically will reduce your attack surface area.
Chatty Devices on Your Network
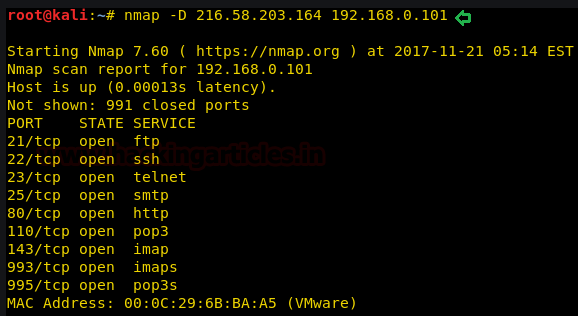
When someone starts scanning your network, the scanner is constantly sending out packets hoping to get a response. Unless the devices on your network are configured to do otherwise, your devices are going to respond with information the scanner can potentially use. It is not just which ports are open, the OS and version can be determined if enough information is available.
The mitigation for this threat vector is to have secure configurations used for your devices. Ideally you would want to have secure images created and have updates done automatically through a device management software like Microsoft Endpoint Manager or Manage Engine.

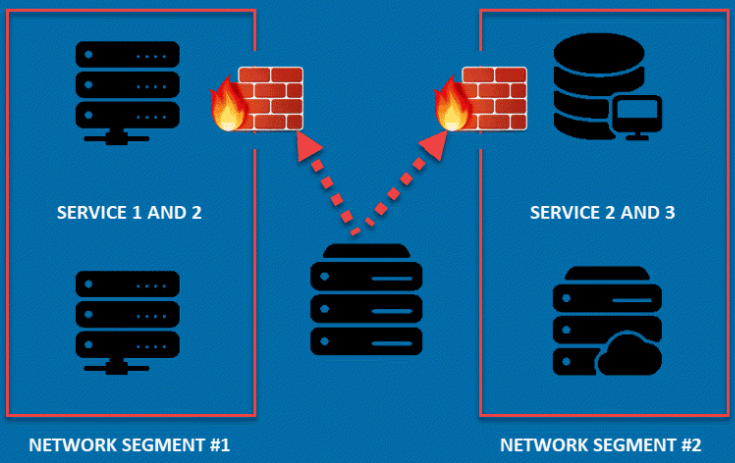
Unsegmented Networks
A network scanner can only scan the devices that it can reach, which is why unsegmented networks are an issue. In an unsegmented network, all devices can talk to all other devices, including the one scanning your network.
The mitigation for this threat vector is to find ways to segment networks that do not need to communicate with each other. This solution can be implemented for free in some networks because a lot of modern network equipment supports logical segmentation to manage both north-south and east-west traffic.
Unmonitored IT Infrastructure
Network scanning is incredibly noisy and obvious on the network being scanned, but that does not matter if no one is monitoring the network. A malicious actor could scan every inch of your network, and you would never know if the right tools are not there or if there is no one monitoring the tools.
The mitigation for this threat vector is to monitor for suspicious activity on your network. There are tools like IDS, XDR, and SIEM systems that can all detect signs of network scanning. If you do not have the time or staff with the skills needed to monitor these tools, consider hiring a cybersecurity services provider like CyberMSI to do it for you.

Scan Your Own Network to See What They See
If an organization scans its own network, they will quickly discover what a malicious actor could see if they ran a network scan. This is a useful exercise because it will outline all the other potential vulnerabilities that the organization did not know about until scanning their own network.
There are many other threat vectors that we did not have time to address in this blog that you can discover on your own by scanning your network. Add network scans to your routine security and risk evaluations to have a better understanding of your vulnerabilities now and over time.
We will continue to share best practices and lessons learned in future posts in the Threat Vector series. Managing the privacy of your network is an important step for securing the rest of the organization.
In closing, consider these three questions when mitigating network scanning in your organization:
- How easy is it to get access to our network?
- Do we have secure configurations for our devices, and if so, do they take network scanning into account?
- Is there enough capacity on our IT and security teams to monitor the network or should we hire a 3rd party like CyberMSI to help?
