CISA Incident Preparedness in Microsoft Sentinel

Make adjustments to your cloud environment to enhance your incident readiness.
Cybersecurity and Infrastructure Security Agency (CISA) is a US government organization that is dedicated to making sure that the nation’s cybersecurity is as strong as it practically can be. CISA routinely produces cybersecurity recommendations that organizations can use to enhance their security and incident preparedness.

In this blog, we will go over the major points of the most recent CISA incident preparedness guidelines and discuss how they can be applied in Microsoft Sentinel. We will also discuss specific tools security administrators would need to use in Microsoft Sentinel to apply the recommended controls.
Account Controls
To reduce the chances and impact of an incident, CISA recommends several account controls.
- Prevention: Unauthorized access to accounts in Microsoft Sentinel can be controlled by implementing features like 2-factor authentication and Protected Users.
- Impact Reduction: Damage caused by a compromised account can be controlled in Microsoft Sentinel by implementing access control features like PIM or Justin-in-Time and doing routine access reviews.
- Monitor: CISA recommends that logs related to identity be collected and monitored in a central location, which in Microsoft Sentinel is their SIEM system Microsoft Sentinel.
System Management
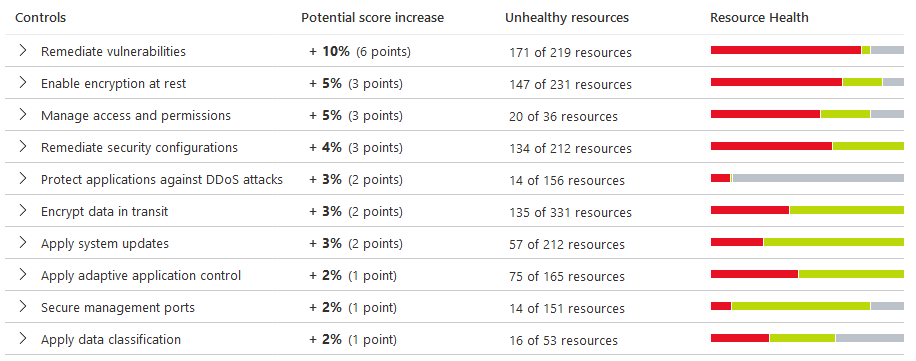
To reduce the chances and impact of an incident involving systems, CISA recommends several system management controls.
- Prevention: Unauthorized access to systems in Microsoft Sentinel can be controlled by creating secure images and routinely patching systems based on Security Center recommendations.
- Impact Reduction: Damage caused by a compromised system can be controlled in Microsoft Sentinel by segmenting systems as much as possible with network security groups.
- Monitor: Ideally a system should be monitored and protected by an EDR/XDR solution, which in Mincrosolft Sentinel is their XDR solution Microsoft Defender for Cloud. It is also recommended that logs from systems be collected and monitored in a central location like Microsoft Sentinel.
Server Configuration and Logging
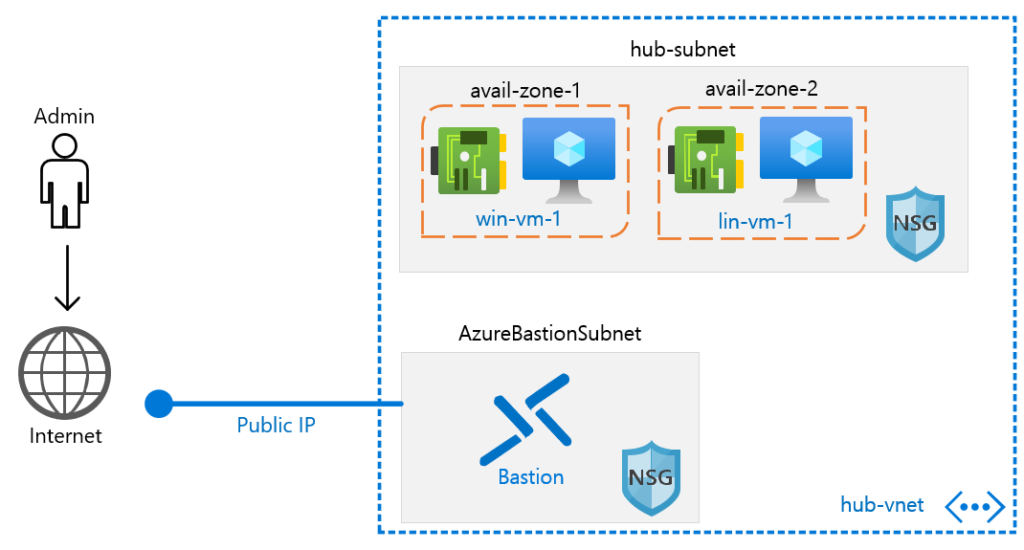
The CISA server configuration recommendations had many of the same items as the system management section. Some server-specific recommendations were added like using jump servers (like Bastion), putting restrictions on admin accounts, and instructions that are specific to Windows or Linux servers. All the server-specific recommendations can be implemented in Microsoft Sentinel by adjusting settings or using extensions.
Network Management
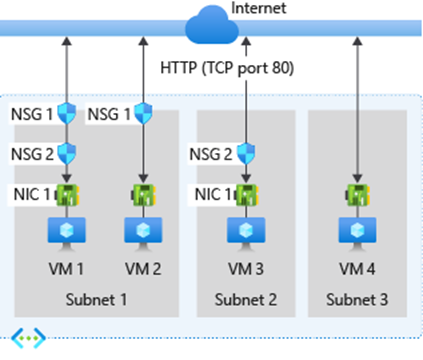
The recommendations for networking were separated into 2 categories that were focused on network controls and infrastructure. The network controls section has recommendations about controlling network traffic using methods like encrypting traffic and doing routine scans.
The infrastructure section has recommendations for implementing secure network infrastructure like creating secure images for network devices and controlling what traffic comes into the network using firewalls in different areas of the network. Microsoft Sentinel can implement all these security recommendations by adjusting the settings for a well-defined set of network security groups.
Procedural Controls
Security has many routine activities that organizations must do to ensure that their controls are working as intended. The CISA recommendations have a procedural section that describes routine activities like vulnerability assessments, access reviews, and maintaining documentation. Microsoft Sentinel has tools for vulnerability assessments (Security Center) and access reviews (Identity Governance), but documentation is the responsibility of the organization using the Microsoft Sentinel services.
User Education
The CISA recommendations include the training you would expect from an organization like being suspicious of downloads from 3rd parties, identifying suspicious emails, and basic incident response instructions. Informed users will be able to help with protecting your cloud resources just like they do for on-premises resources.
We will continue to share best practices and lessons learned in future posts on implementing security recommendations. CISA is one of the many organizations that CyberMSI is monitoring regularly for the most up to date security recommendations.
In closing, consider these three questions when implementing CISA recommendations in your organization:
- Are we able to get other key members of the organization onboard with implementing these CISA recommendations?
- Do we have someone available that knows enough about cloud security to implement these recommendations in Microsoft Sentinel?
- Will we be able to implement the procedural controls in these recommendations on a regular basis?
