Threat Vector: Dumpster Diving

One man’s trash is another man’s breach.
The term “dumpster diving” is used to refer to looking through discarded items from the organization to get additional information. A malicious actor does not necessarily have to go through a literal dumpster to find information discarded by the organization, but it is a good place to start.

In this blog we will discuss how an organization can prepare for potential dumpster diving techniques that malicious actors can use to gather more information about their environment. We will also discuss potential mitigations that organizations can implement to mitigate this threat vector.
Literal Dumpster Diving
The term dumpster diving was made back when paper records were more prevalent, so some organizations may not be as concerned about securing their trash now that their records are electronic. This is a mistake because many users still need paper for their job, and there are other items with information in them that could be thrown away.
In a supposedly paperless organization there is still paper mail, post-it notes, and removable memory that users could throw away. The mitigation for this threat vector is to secure your trash with at least a lock. There are other ways organizations could secure their trash like incinerating higher-risk trash and hiring a more security-focused waste disposal company.

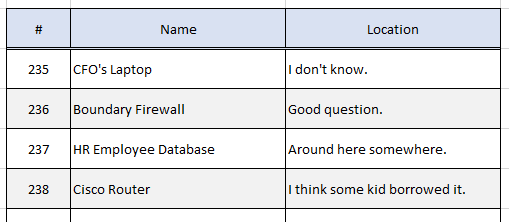
Abusing Loose Inventory Management
What many organizations do not consider is that if inventory management is not followed strictly, their inventory can be accidentally disposed of. While studying for his CCNA the author of this blog got a free industrial-sized router from a relative’s company to practice on because the company was not keeping track of their old inventory.
The loosely tracked inventory resulted in a router with information about the organization’s network and network device configurations leaving the organization without anyone knowing. The mitigation for this threat vector is to have a reasonably strict inventory management system implemented and making sure that the IT staff understand why the inventory management system is important.
Abusing Loose Inventory Disposal
Some organizations are either not aware of or do not care about the information on their disposed of hard disks. If an organization is mass-disposing of devices without disposing of the hard disks they are painting a target on their back.
Once the hard disks leave the building the organization has no way of controlling what happens to the information on the hard disks. The mitigation for this threat vector is to dispose of the hard disks fully using methods like degaussing or destruction.

Electronics Recycling
Electronics recycling can be both a location to go dumpster diving and a social engineering opportunity. Less reputable people that are collecting recyclable electronics could be paid off by or working with someone that can take advantage of information on your organization’s electronics.
A malicious actor could also pretend to be an electronics recycler and get friendly with your IT staff so that they will trust them with the electronics that are being disposed of in your organization. The mitigation for this threat vector is to have inventory disposal procedures enforced and only work with reputable electronics recycling organizations.

Disgruntled Employees
When an employee makes an angry post on social media about quitting their job, their trash could become a target as well. If they are in a blind rage, they are very likely to throw out company equipment like laptops and other information without thinking about the consequences.
The mitigation for this threat vector is to make the NDA that your organization members sign more specific so that it includes other items that contain sensitive information.

We will continue to share best practices and lessons learned in future posts in the Threat Vector series. Staying on top of inventory and disposal will leave less opportunities for malicious actors to get information from your organization’s trash.
In closing, consider these three questions when mitigating dumpster diving in your organization:
- Are there any security controls on our trash disposal?
- Do we have inventory and disposal management procedures in place in our organization?
- If I were a malicious actor, where would I look for discarded information from an organization that I am targeting?
