Why Am I Not Getting Alerts in Defender for Office 365?

Discover How to Monitor All Your Email Incidents.
Analysts at CyberMSI had recently set up a test environment for Defender for Office 365 with roughly 10 users in it. They found that the test environment was receiving as high as 40 phishing emails a day without any of them generating an incident in the 365 Security Incidents menu or in the Microsoft Sentinel SIEM it was connected to.
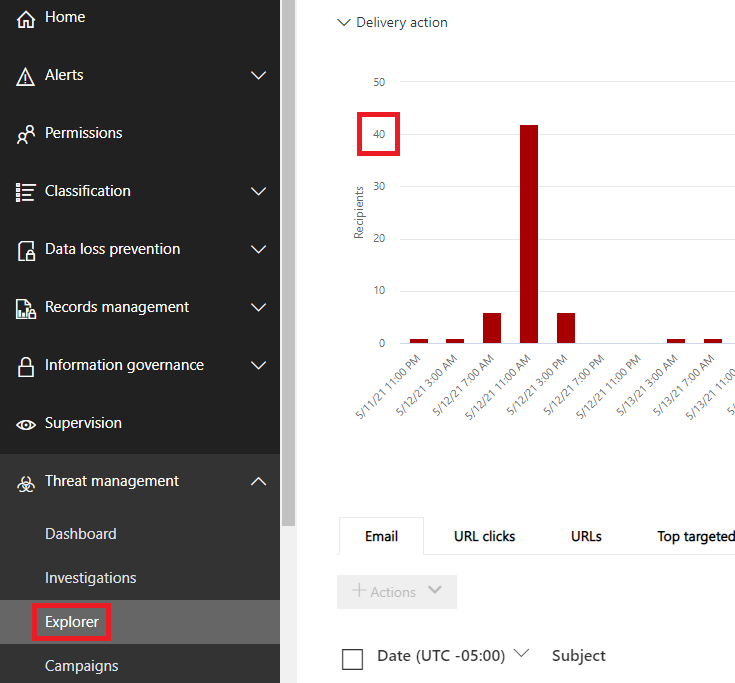
Having detections that do not generate alerts or incidents is a practical decision from Microsoft’s perspective. There would be a massive flood of alerts and incidents if they were generated every time a potentially malicious email was detected. However, one of the drawbacks of this decision is that detections do not appear in 365 Security Incidents or Microsoft Sentinel. Consequently, organizations cannot rely on their XDR and SIEM systems to know about the volume of potentially malicious emails that they are getting.
In this blog we will discuss how the detections, alerts, and incidents work in Defender for Office 365 so that you can use this information to get a better view of the malicious emails coming into your environment. We will also discuss practical steps that security administrators can take to manage the volume and type of email alerts they are getting.
Built-In Detections
Defender for Office 365 determines which emails are potentially malicious using its built-in detections. The detections will look for specific emails that it believes could be malicious and records those detections in the 365 Security Explorer menu.
Users can access this menu and adjust the “View” option near the top of the menu to see what different types of detections have been going off over time. This menu is useful for determining what kind of potentially malicious activity in your environment could be turned into alerts.
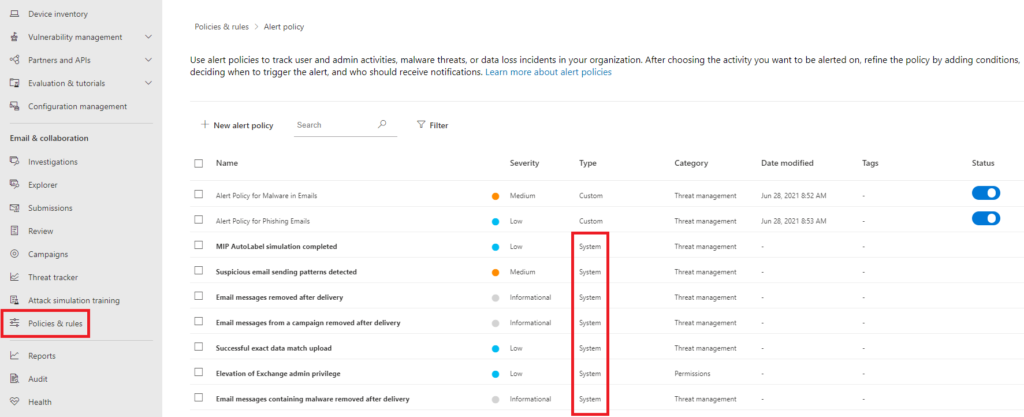
Built-In Alert Policies
The detections do not turn into alerts unless they have a policy set in the Alert Policy menu. There are roughly 40 built-in alert policies that create alerts and incidents when they find a specific type of malicious activity.
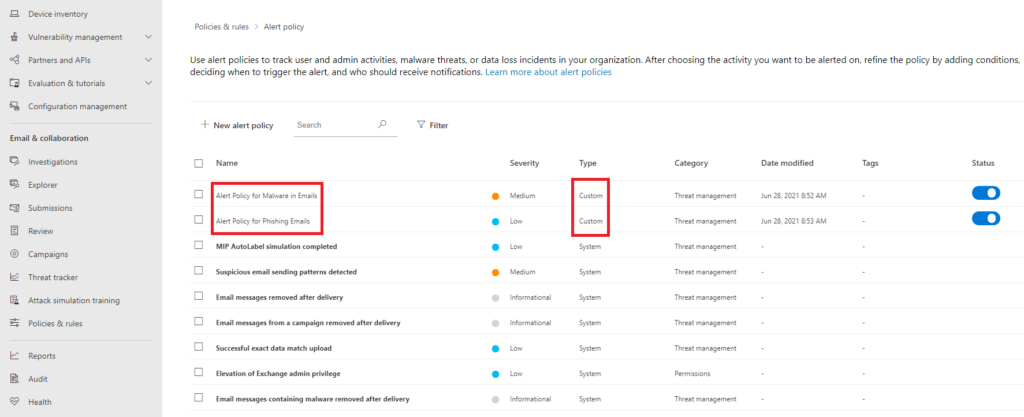
Custom Alert Policies
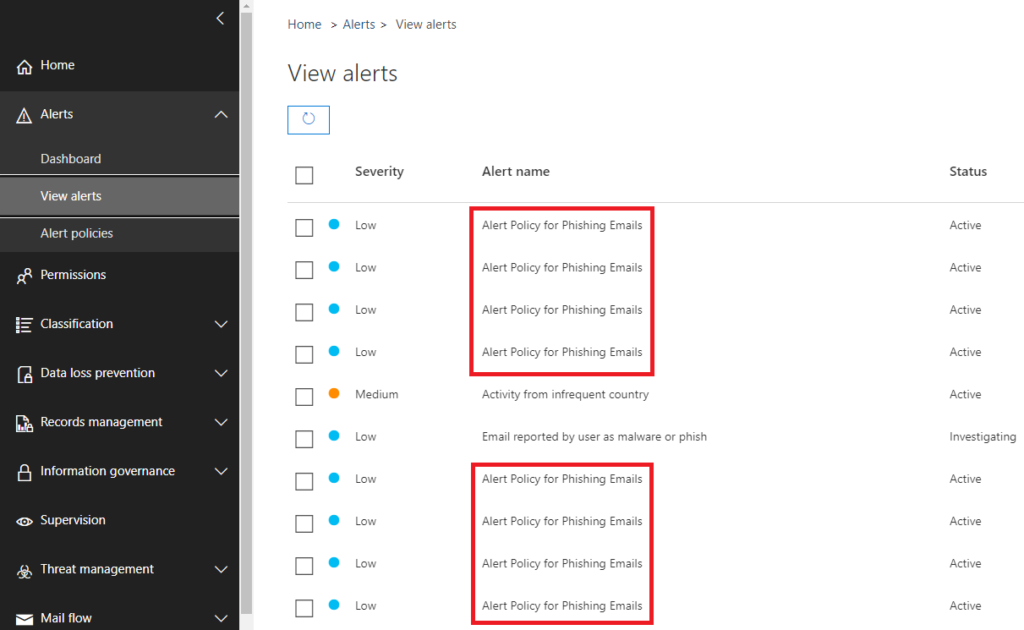
If a security admin wants to generate alerts based on the detection activity that they see in the Explorer menu, they will have to create a custom alert policy. Custom alert policies use conditional logic, and when the condition is met, they generate an alert but not an incident.
In the example image there are 2 custom policies that generate alerts if phishing or malware activity is detected in an email. They generate many alerts, so it is important to add more conditional logic to reduce the volume and false positives in the generated alerts.
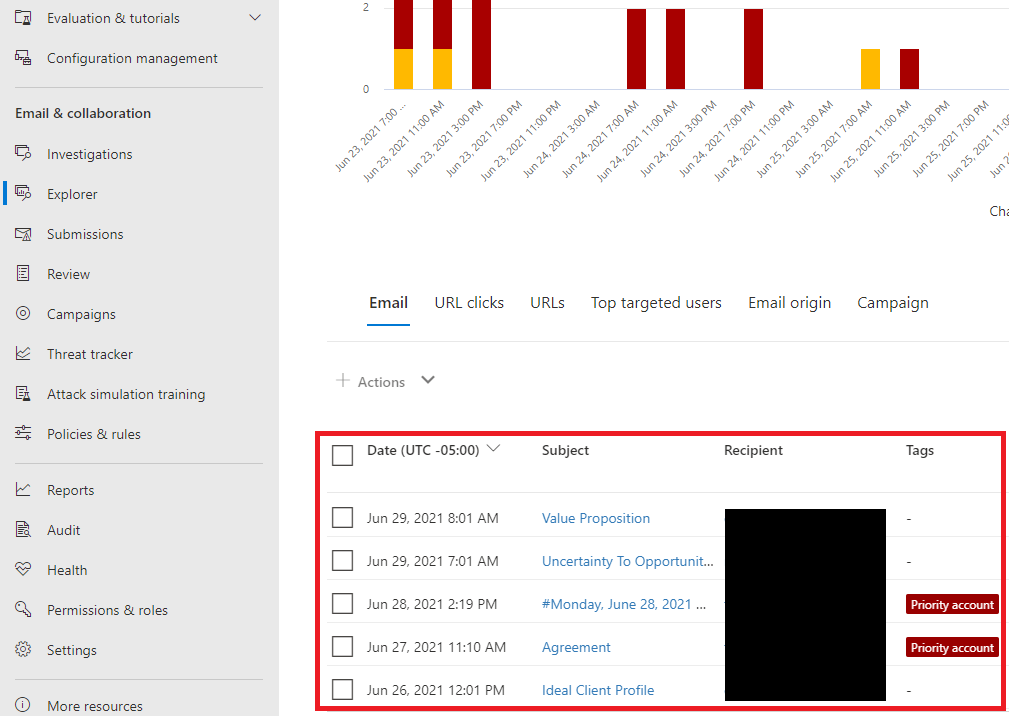
Using Explorer to Make Alerts from Detections
When attempting to create custom alerts in Defender for Office 365 it is important to go through the types of emails that are being detected. By analyzing the data in these tables, security administrators can discover common features that can be used to reduce the volume of alerts and the number of false positives.
Transitioning Alerts to Incidents
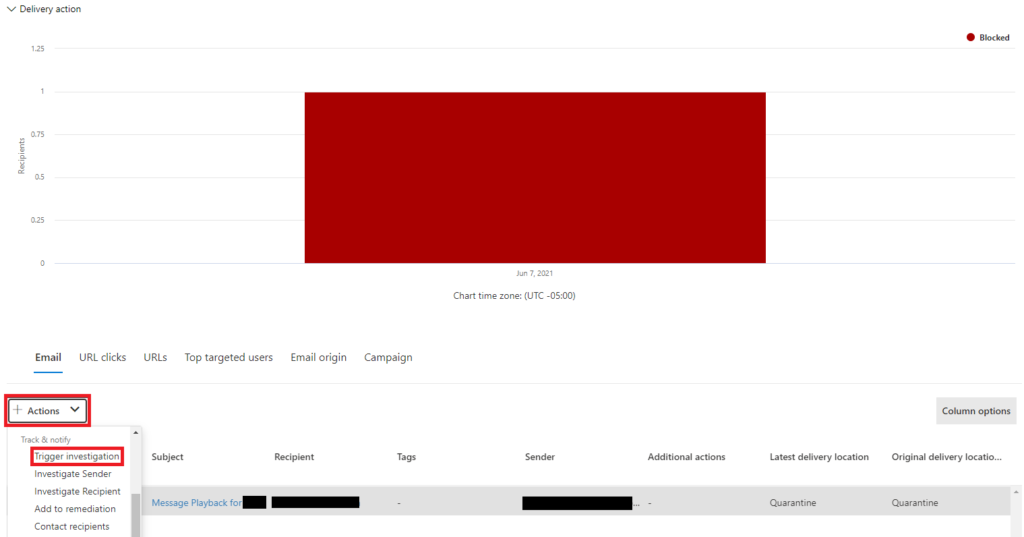
Custom policies unfortunately do not generate incidents on their own. If an analyst wants to investigate the alert as an incident, they will need to locate their incident and start an investigation in Explorer using the Actions drop-down menu.
Handling Email Incident Volume
Since organizations are receiving a high volume of potentially malicious email and the detections are not perfect, there will be a high volume of alerts that will appear in your analysts’ queues. It is the responsibility of security administrators and management to come up with ways to lessen the impact of having these many alerts.
Volume can be managed by creating additional filtering logic when creating alert policies. There are also options like changing the responsibilities and SLAs of analysts when it comes to email incidents based on the risk appetite of the organization that is being monitored.
We will continue to share best practices and lessons learned in future posts on managing email incidents in customer environments. We are constantly monitoring and testing the capabilities of Defender for Office 365 to give our customers the best possible email incident response services.
In closing, consider these three questions when using Defender for Office 365 alerts and incidents in your organization:
- Do all the cybersecurity analysts know how to use the Explorer menu to find malicious emails in the Exchange environment?
- Is it advisable to set up alerts for the types of emails that we are not being notified about now?
- How can we limit the volume of email alerts that we are getting so that we do not overwhelm our security analysts?
